Yang Luo A passionate generalist
I. Research & Engineering Projects
4. PenetrationTest
Back
Jan 2012 - Apr 2012
BUAA, Key Laboratory of Beijing Network Technology
Project Description: The project mainly researched on the automatic generation and execution of penetration test scheme, during the scheme enforcement, vulnerability and penetration process can be combined and springboard technique is utilized for further penetration.
Responsibility: I am In charge of the development team which consists of three postgraduate members.
Introduction: PenetrationTest is a project of KLBNT. Its main purpose is to integrate vulnerablility scanning with penetration. PenetrationTest uses Nessus for vulnerability scanning and Metasploit Framework for penetration. After port scanning, Nessus will genrate a XML format scanning report. And we develop a ruby software to Parse the report and generate a penetration test scheme which adopts the pts file format. We also developed a MFC software named PenetrationTest to parse the pts file and send instructions to Metasploit server-side daemon process. Metasploit will implement the penetration and send back the results to PenetrationTest. PenetrationTest is able to draw a penetration graph which shows the penetration path according to the results returned from Metasploit.
Languages used by PenetrationTest are:
C/C++
ruby
Techniques used by PenetrationTest are:
MFC for UI
Winsock API for communications with Metasploit
GDI API for drawing penetration graph
Useful links:
Download source from GitHub
https://github.com/hsluoyz/PenetrationTest
Metasploit official website
http://www.metasploit.com
Nessus official website
http://www.tenable.com/products/nessus
Ruby official website
http://www.ruby-lang.org/en
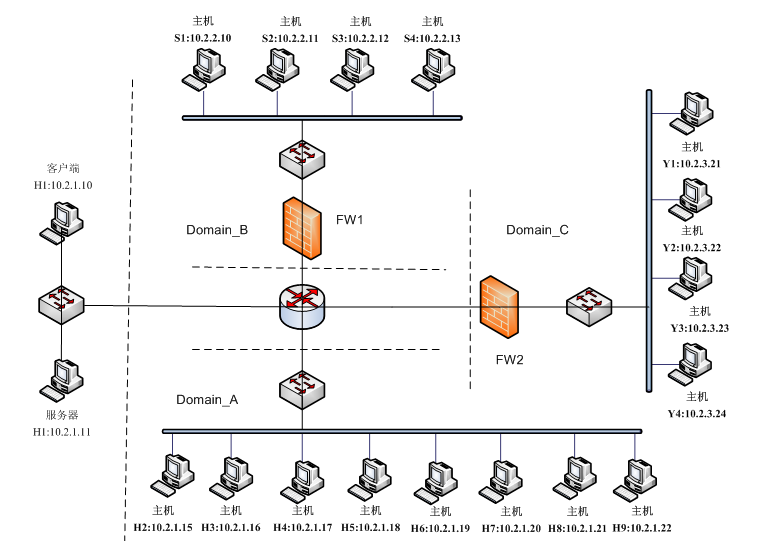
Fig.1. The structure of experimental network topology.
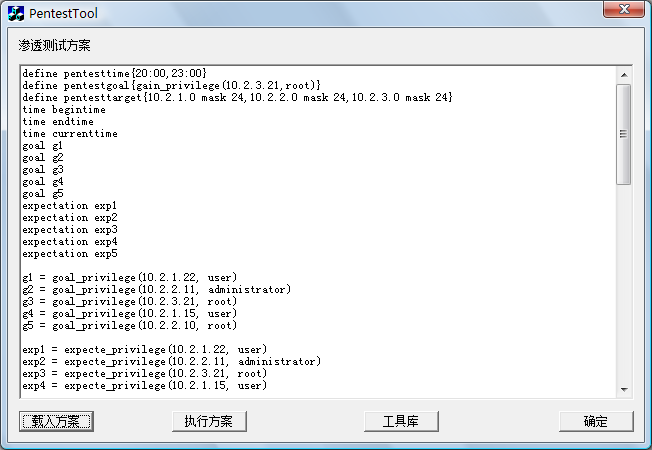
Fig.2. The main window of PenetrationTest.
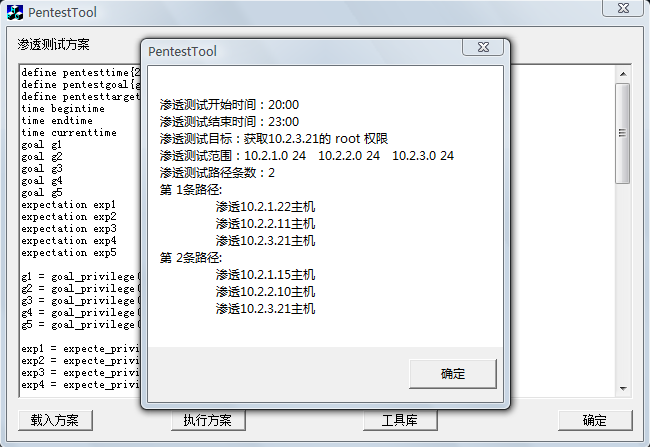
Fig.3. The information parsed from .pts penetration scheme file.
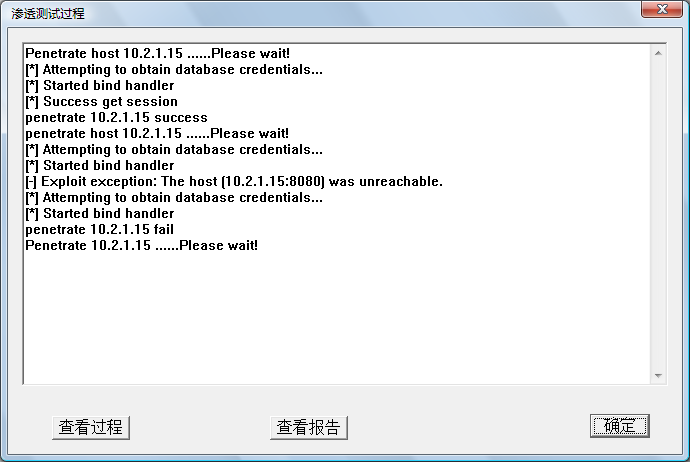
Fig.4. The penetration procedure window of PenetrationTest.
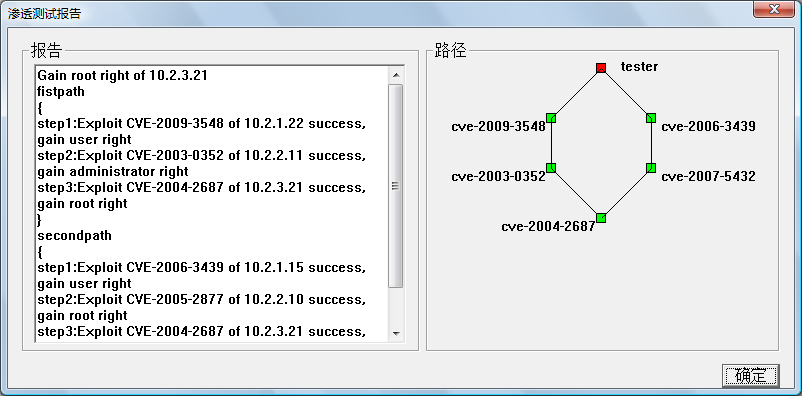
Fig.5. The penetration report windows of PenetrationTest.
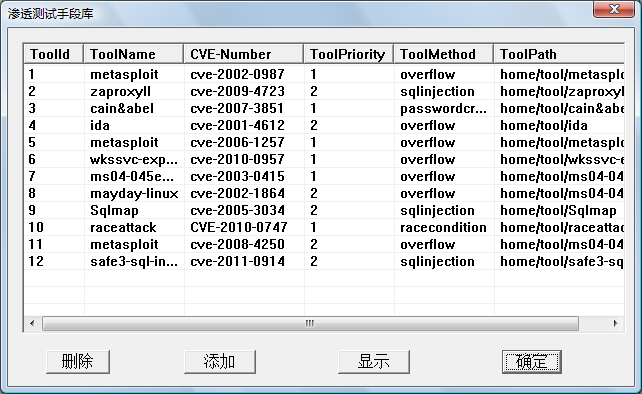
Fig.6. The penetration measure window of PenetrationTest.
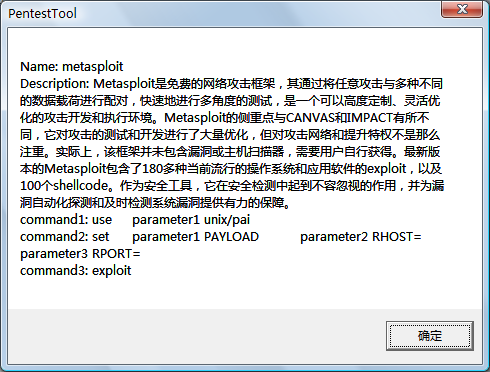
Fig.7. The penetration tool window of PenetrationTest.
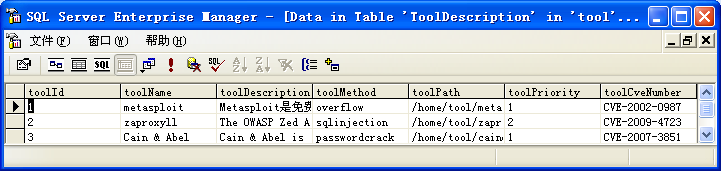
Fig.8. The SQL Server database used by PenetrationTest.
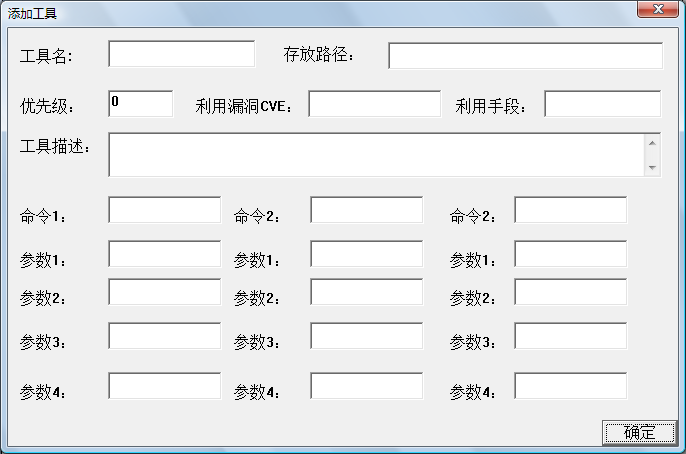
Fig.9. The penetration measure adding window of PenetrationTest.